Report script security
FastReport .NET supports calculation of expressions for displaying values in the desired form, or any object visibility conditions. It is also possible to process events for each object of the report, e.g., before printing it. Event handlers are placed in a report script that supports C # and VB.NET languages. In addition to processing events, the script can contain almost any calculations or actions that can generate the necessary data or change the report behavior, as is required by the developer of the report template.
Before building the program in the report script language, the report generator takes into account all expressions, functions, and calls to parameters in the report. Then the program is combined with the script that the report template developer had written. The resulting script is compiled and loaded as a library into the application that works with the report generator.
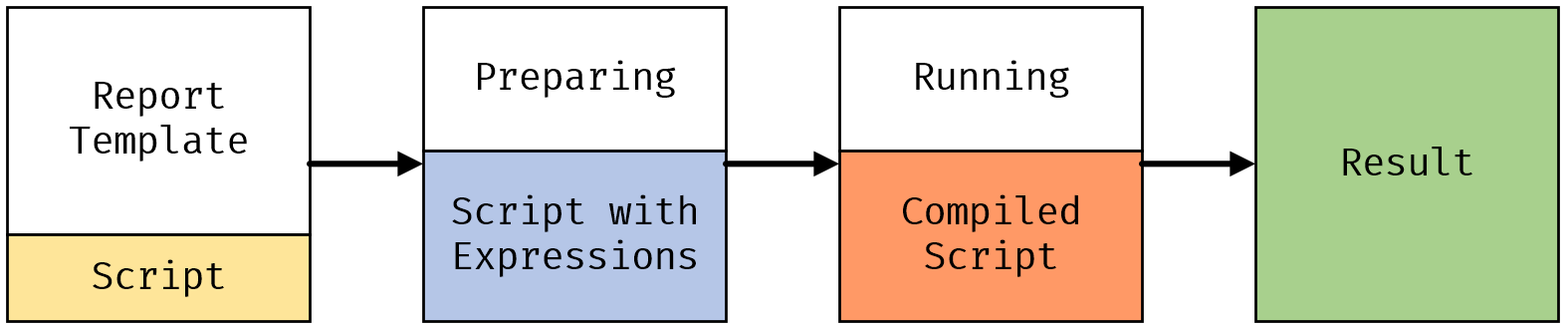
When you run reports in web applications, you can edit them using the Online Designer. Editing is carried out using a browser, the edited report is sent to the server and then can be built there.
While reports are edited by trusted developers and run in an isolated environment, the ability to use scripts in reports gives you freedom and almost unlimited possibilities for data processing and visualization. Editing and execution is under control. As soon as the possibility of general access to editing reports through the browser and Online Designer appears, the question of the building reports security on the server arises. It becomes possible to inject malicious code into script and report expressions.
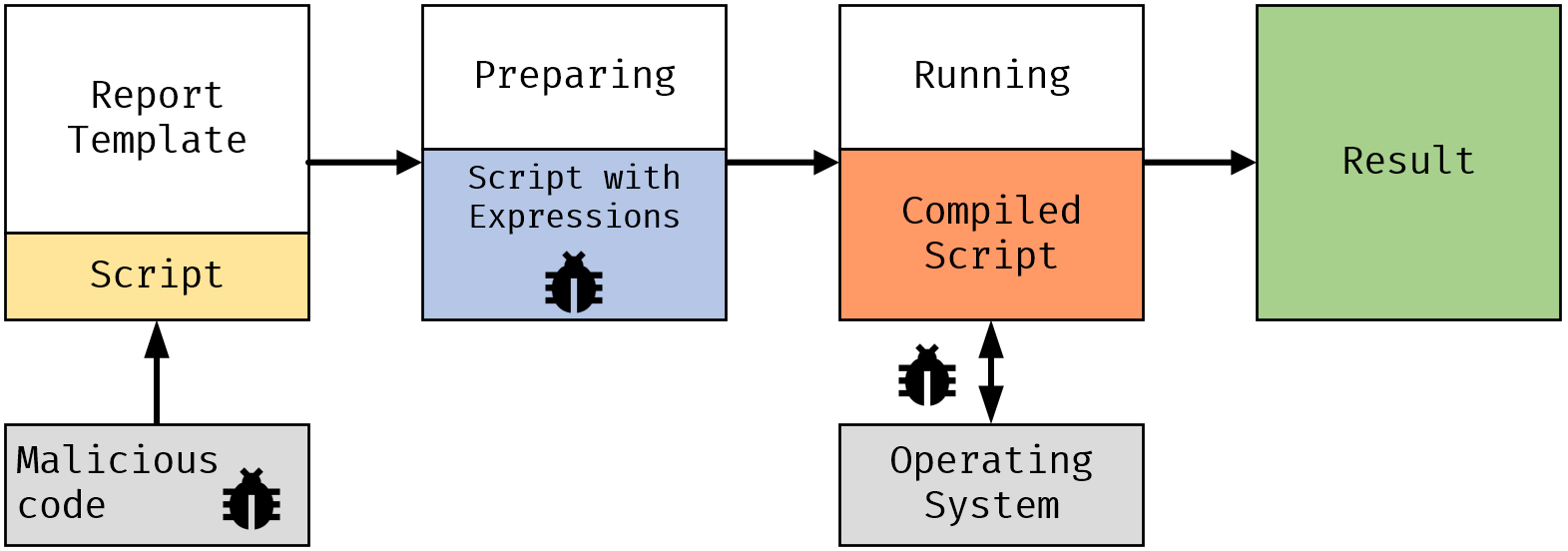
To prevent the execution of malicious code in the script and report expressions when working on the web, special security features have been added in FastReport .NET 2020.3.22. The changes concern FastReport .NET, FastReport .NET Core, FastReport Mono and FastReport Open Source.
Security features are active by default, but developers can change or disable them as needed in their applications.
New properties and methods:
bool FastReport.Utils.Config.EnableScriptSecurity – enables or disables checking of the report script. Works only when reports are running in web applications
(FastReport.Utils.Config.WebMode == true). This property is set True by default (enabled).
event FastReport.Utils.Config.OnEnableScriptSecurityChanged – the event is triggered when EnableScriptSecurity has been changed. Can be used for additional security controls.
FastReport.Web.WebReport.SetScriptSecurity(IScriptChecker scriptChecker) - Installs a custom implementation of a verification method that overrides the built-in security controls.
ScriptSecurityProperties FastReport.Utils.Config.ScriptSecurityProps - parameters for configuring the script security check. Is set NULL if a non-web application is running. (FastReport.Utils.Config.WebMode == false).
bool FastReport.Utils.Config.ScriptSecurityProps.AddStubClasses – enables or disables adding stub classes for the script. This property is set True by default (enabled). Not overridden by setting your own SetScriptSecurity handler (see above).
event FastReport.Utils.Config.ScriptSecurityProps.OnStopListChanged – the event is called when the StopList has been changed. Can be used for additional security controls.
string[] FastReport.Utils.Config.ScriptSecurityProps.StopList - a list of keywords that should not be used in the report script. Contains a default list of words.
FastReport.Utils.Config.ScriptSecurityProps.SetDefaultStopList() - sets the default value of the StopList (discards changes).
The developed report script protection complex allows to minimize the threat of malicious code injection and its execution on the server side.
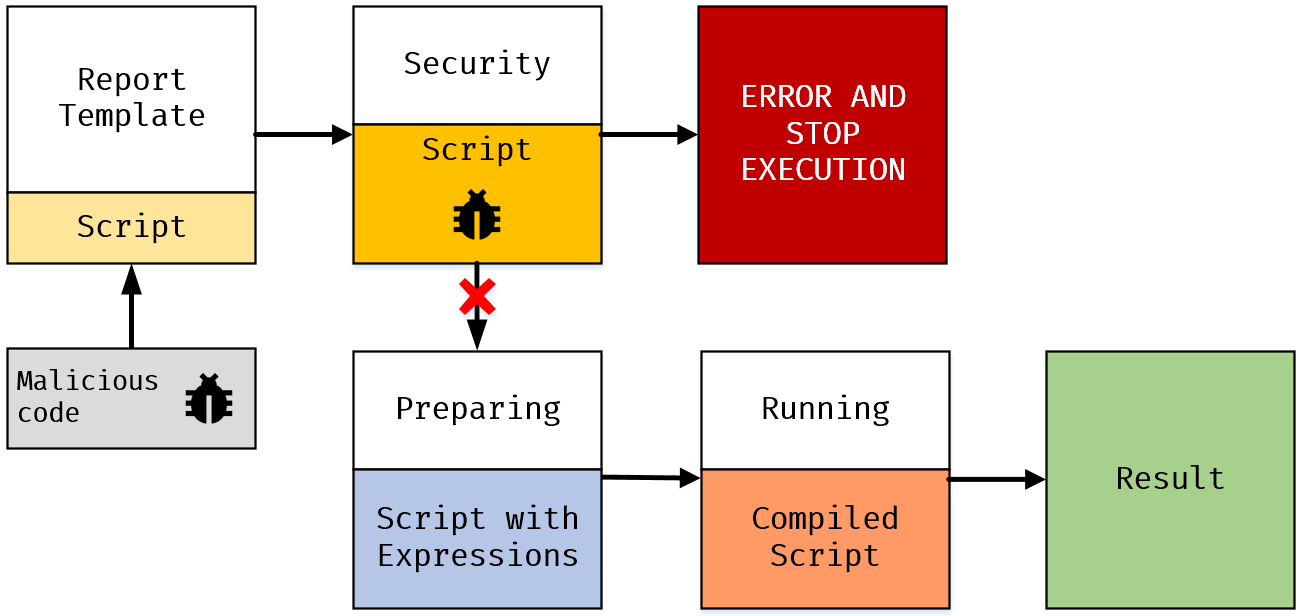
It is necessary to remember that even the use of built-in report script security controls does not provide one hundred percent protection against the injection of malicious code into the saved templates. Therefore, we strongly recommend keeping access logs in web applications and allowing a limited number of privileged users to edit report templates.